This registry key allows to selectively disallow dynamic updates for resource record types. i,e using the reg key can prohibit dns dynamic update of certain resourse record types.
By default, In
windows 2000, For unsecure zone, Allows dynamic updates for NS, SOA, and server host records. For secure zones, allows dynamic updates for root NS and SOA records and allows delegations and server host updates for both zones. But in
windows 2003, For standard unsecure zones, prohibits all update policy options. For secure zones, only SOA and zone root NS updates are allowed.
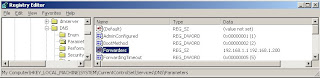
Key Name: UpdateOptions
Type: dword
Default: 0x30F
Functionality: Prohibits dynmic updates by bit masking reg value. Each bit in reg value prohibits one type of record.
Location: HKLM\SYSTEM\CurrentControlSet\Services\DNS\Parameters
This reg value is a bitmask value. Each bit in this, corresponds to a particular resource record.
To disable or enable DNS dynamic update on a certain record type, set or unset the corresponding bit in the reg value.
The following shows bit position and it's corresponding record type
For standard nonsecure zones:Reg Value Meaning0x1 Allows SOA (Start of Authority) records.
0x2 NS(name server) records
0x4 Delegation NS records.
0x8 Host A records in the DNS server's own host record.
For secure zones:Reg Value Meaning0x100 SOA records.
0x200 NS records.
0x400 Delegation NS records.
0x800 A (address) records in the DNS server's own host record.
Other general values irrespective of zone typesValue Meaning0x0 Allows DNS dynamic update on all record types.
0x30F Prevents all of the update policy options for unsecure
zones, and allows only SOA and zone root NS updates for secure zones.
0x1000000 Prevents the relay to a DNS server's peers of the server's A record updates.
To set the reg key value to say 0x0, do
reg add "HKLM\SYSTEM\CurrentControlSet\Services\DNS\Parameters" /v UpdateOptions /t reg_dword /d 0 /fNote: 1. Direct changes to registry key will be effective only after rebooting the dns server.
2. DNS Manage console can be used to set the value for UpdateOptions and get that
effect without having to restart the server.